Cybersecurity
The technological advancements, ever growing dependence on technology, rapid growth of the Interne and mobile technology, and the progressively intertwined integration amongst devices and information over...
Read More


Technology has become an integral part of the daily life of everyone irrespective of their generation and built-in the DNA of any organization. The rise of the digital era has transformed the landscape of all industries and market sectors, making the digital presence a need as opposed to an accessory; which is evident in the flourishing of e-commerce and global reach of social media that have contributed to the success of many businesses and the demise of many who could not or chose not to ride the wave of change.
The rise of the internet of things (IoT), wireless technology and cloud services presented further opportunities that have are also associated with risks that need to be monitored and managed.
Driven by the need to provide value for their stakeholders and satisfy the regulatory requirements, governments for example, have embarked on a race, not only to automate their services, but to transform into smart governments and this innovative drive is continuing towards creating smart cities and potentially countries.
Banks and financial institutions progressively maintain and safeguard a large volume of personal and financial information and they are responsible towards their customers, stakeholders and regulators to safeguard this information, protect their privacy and provide assurance that the respective risks are being effectively managed.
Defense and aerospace industries deal with sensitive information that are controlled by intellectual property and special protocols to ensure the privacy and safety of such technology; hence, a more stringent and proactive risk management protocols should be in place to manage these risks.
Government agencies, social media platforms, e-commerce businesses, fitness and recreational facilities, construction companies, hospitals and medical services institutions, and list continues of the different organizations that maintain critical information which make them the target for cyber-threats.
The need to manage technology, data integrity and privacy risks flow across the whole supply and value chain for any industry, as a breach of sensitive information may occur at a suppliers’ level for who fails to maintain adequate risk management measures. This in turn prompts organizations to more effective contract management measures and procedures.
This digital revolution and rapidly evolving technology bring new opportunities that if not embraced, would jeopardize the business continuity of any organization. Alongside these opportunities emerge a suite of continuously evolving risks which, dependent on how they are managed, would make the difference between thriving or failure of any organization.
Data fraud and/or theft, critical information infrastructure breakdown, cyberattacks and the adverse consequences of the technological advancements are some of the risks that are globally recognized to be some of the prominent risks associated with technology.

The technological advancements, ever growing dependence on technology, rapid growth of the Interne and mobile technology, and the progressively intertwined integration amongst devices and information over...
Read More
Business processes are progressively being streamlined and automated through Enterprise Resource Planning (ERP) solutions, which in turn are rapidly evolving to cater for specific industries' processes and the global...
Read More
As organizations grow and increase their geographical reach, whether organically or through acquisitions and mergers their structures get more complex and the technology platforms protocols...
Read More
How many times have you come across the term "The Internet of things (IoT)" while you are browsing on the net, over the radio, reading a magazine or simply over a casual conversation Whilst to some...
Read MoreAt RISKTAL we work closely with you and advise on how to effectively manage technology risks and achieve a state of cyber resilience through a suite of services in the areas of:

Business processes are progressively being streamlined and automated through Enterprise Resource Planning (ERP) solutions, which in turn are rapidly evolving to cater for specific industries' processes and the global demand for better information that enhance the decision making capability and allow for more stringent control of the business performance.
In recent years, business intelligence tools and solutions have become more prominent and the focus of major ERP developers to enhance the value and appeal of their ERP solutions.
With many of the processes being automated, there is ultimate reliance on the controls imbedded within these ERP solutions. Whilst the ERP developers attempt to develop an off-the-shelf solution based on a detailed risk assessment and model designed controls, rarely do organizations adopt the better practice model, and tend to adapt the system to fit their existing business processes; hence, compromising system controls.
At RISKTAL we work closely with you to assist in finding the better most relevant solutions for your technology issues. Our services are based on global better practices, frameworks and standards and are in the following areas:

The technological advancements, ever growing dependence on technology, rapid growth of the Interne and mobile technology, and the progressively intertwined integration amongst devices and information over the internet gave rise to increased and more advanced forms of cyber-threats; hence, at RISKTAL we look at cyber security in a more holistic manner that involves:
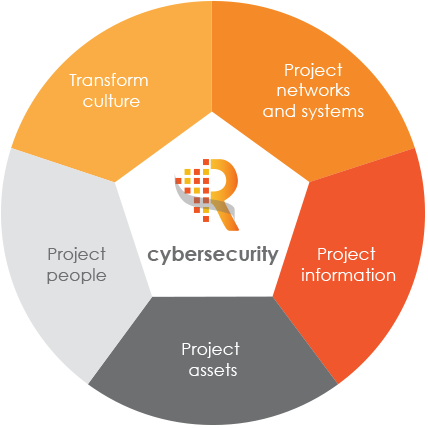

As organizations grow and increase their geographical reach, whether organically or through acquisitions and mergers their structures get more complex and the technology platforms protocols might not be compatible which expose the organization to increased information risks.
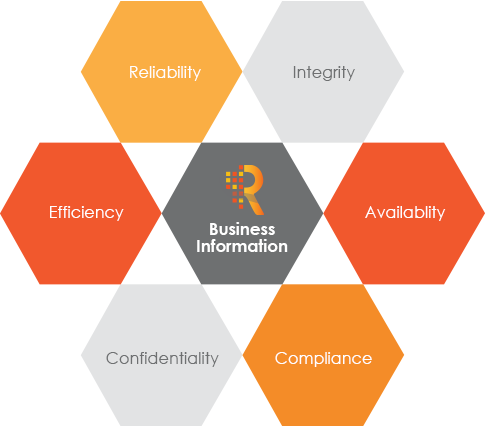

How many times have you come across the term "The Internet of things (IoT)" while you are browsing on the net, over the radio, reading a magazine or simply over a casual conversation. Whilst to some it sounds too generic, this term represents a way of creating and relating digital information to the physical or tangible world.
The internet of things has created value, enhanced performance and optimized many processes across industries, and the examples of that are evident in businesses and in our day to day life:
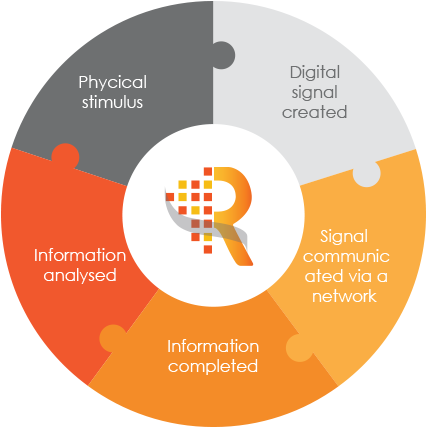
The IoT is subject to a suite of risks at the different stages of the information cycle, predominantly: